Security Operations Center (SOC)
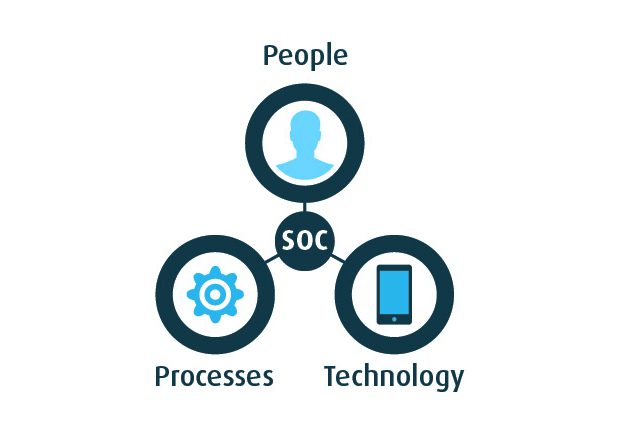
SOC or SOCaaS is a service that provides real time monitoring, detection and analysis of cyber security threats. This service goes above and beyond by a reactive and proactive detection of advanced targeted attacks that have gone undetected by existing perimeter controls. It comprises the three pillars: People, Process, and Technology for managing and securing the organization’s assets and data.
Cyberthreats are evolving nowadays and take lots of challenges, investment and expertise to be able to defend against them.
SBS SOC team will integrate with all your environment critical assets in order to extract logs to SBS Secure Cloud. The Logs from different applications will be processed by the Security Platform.